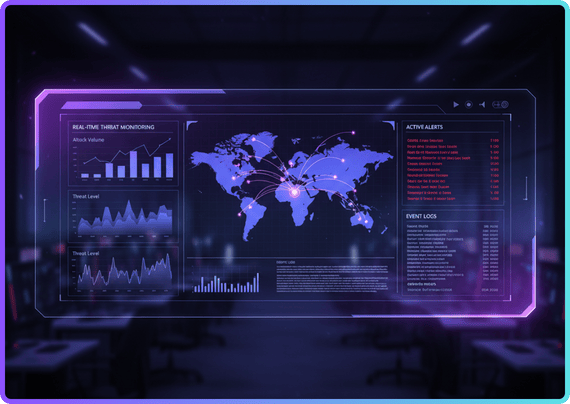
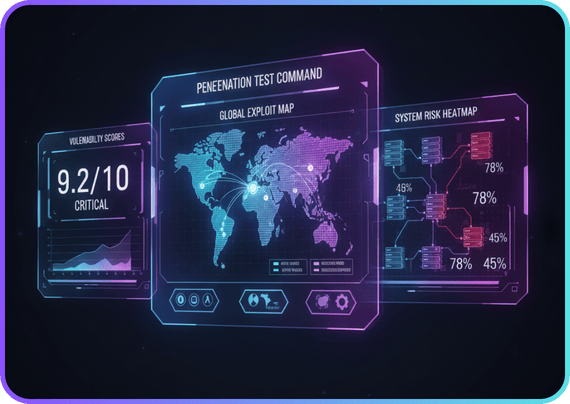
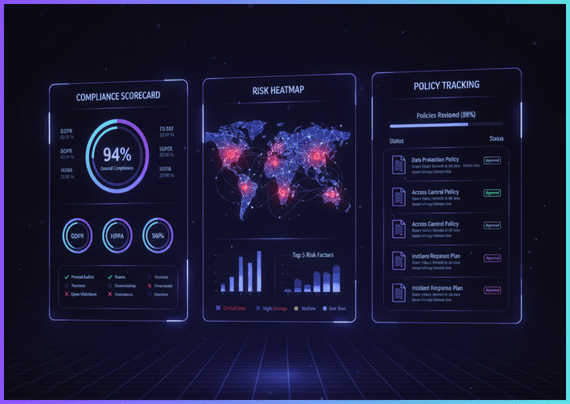
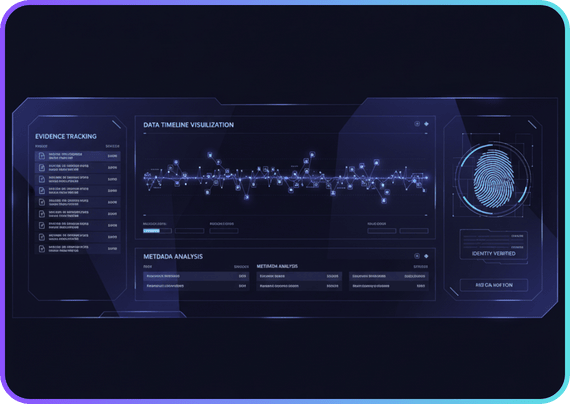
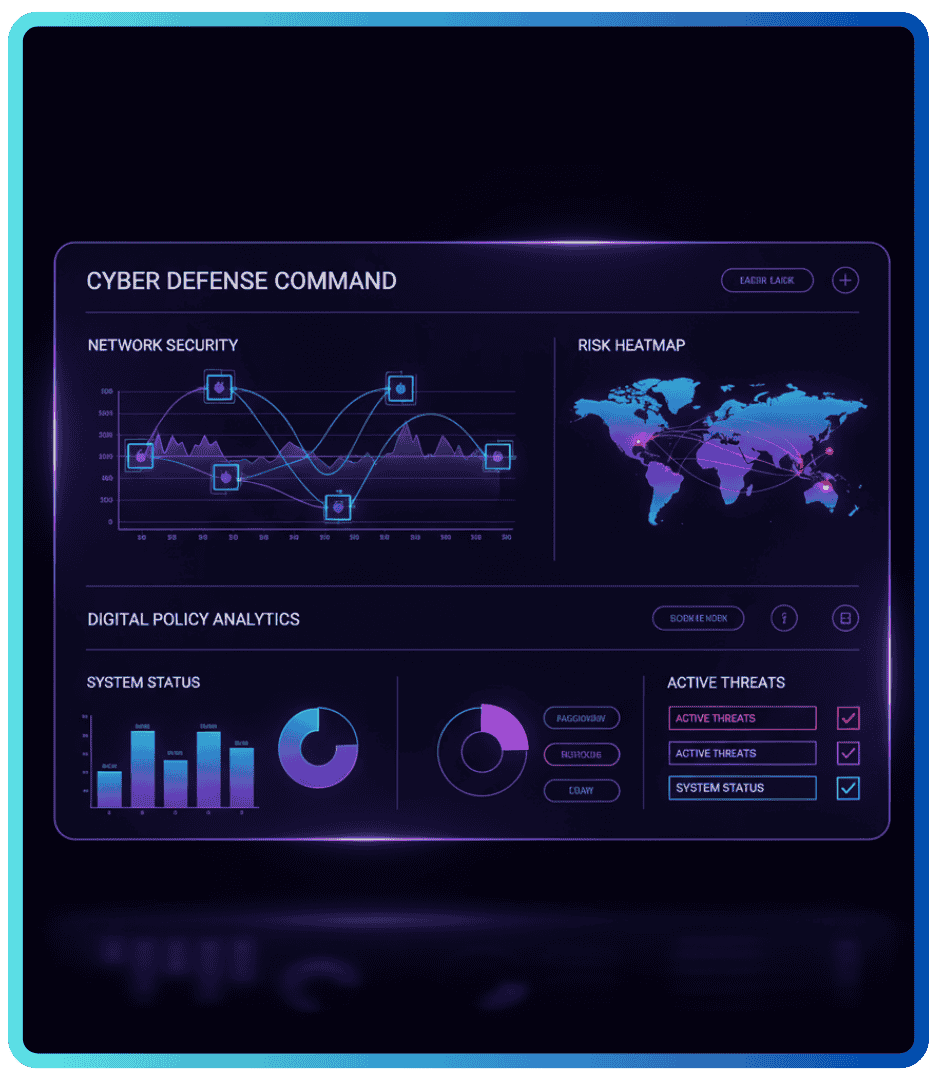
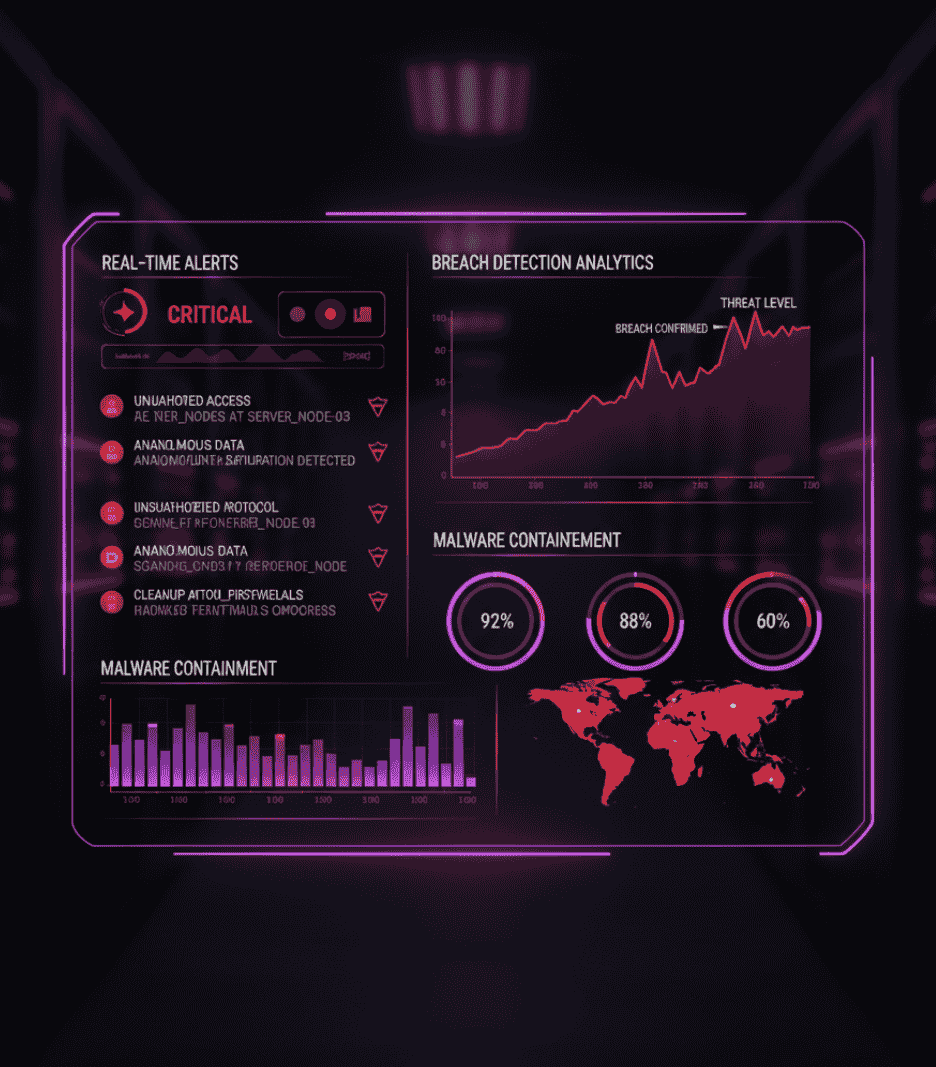
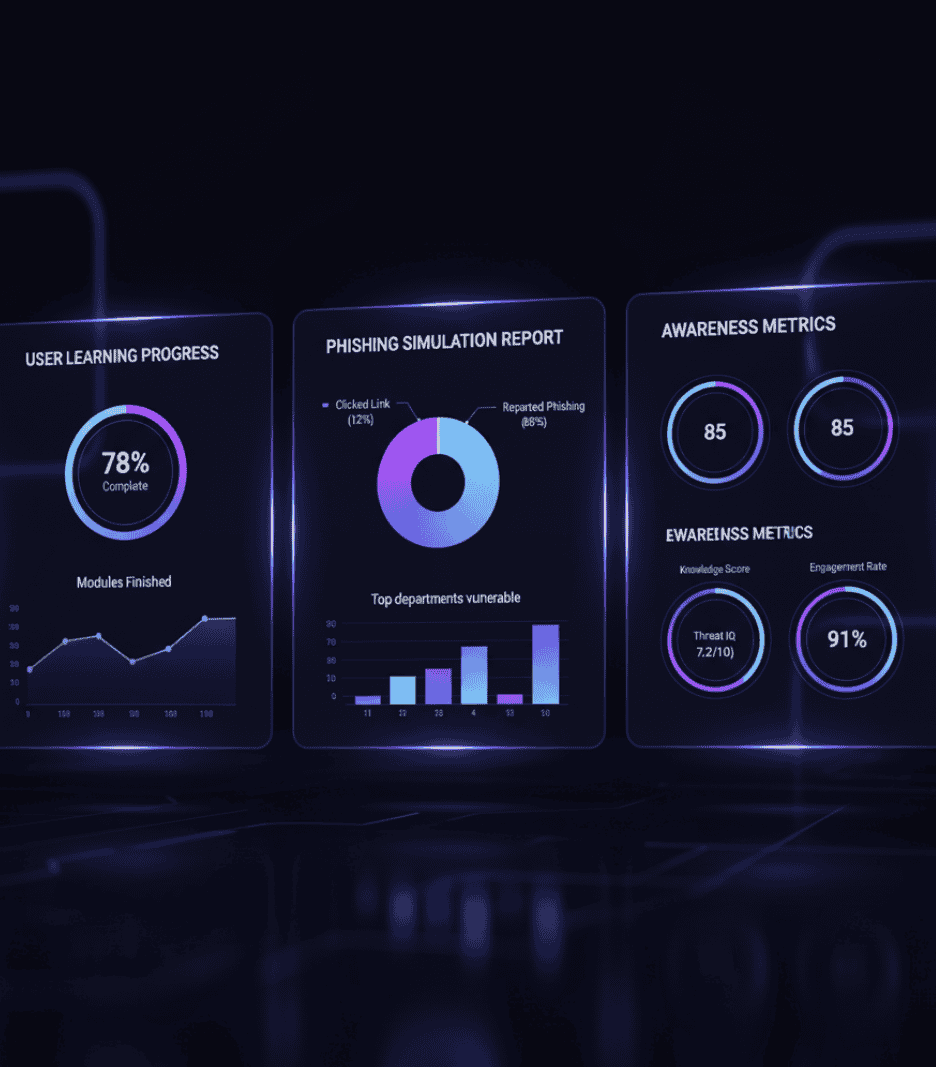
Cybersecurity Consulting
We help organizations evaluate their security posture and create tailored cybersecurity strategies. From infrastructure to policies — we make security scalable and effective.
Key Focus:
- Risk analysis
- Security roadmap
- Implementation guidance